HyTrust Appliance
I had the pleasure of having Eric Chiu and Ken Crandall of HyTrust (http://www.linkedin.com/companies/hytrust & http://www.hytrust.com/) give me a pre-release demo of their soon to be released product, the HyTrust Appliance. I hesitate to call the device a “security appliance”, although it is – and much more. My take on the HyTrust Appliance is that it is a device (either a physical hardware appliance or a VM appliance) whose goal, at a high level, is to provide a centralized point for administrative access to your VMware Infrastructure components. Why would you want such a thing? Here are four good reasons:
- To enable a single authentication source for all of the different administrative access methods (vCenter Server, ssh, web access, VIC, third-party tools, etc.)
- To enable a granular authorization service for users, regardless of administrative access method
- To provide a template-based security configuration for your hosts, and
- To provide a centralized logging facility to simplify and enhance auditability.
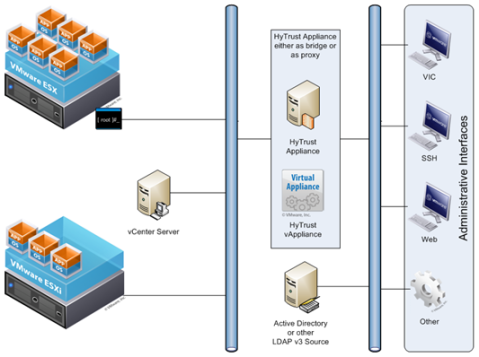
The architecture is relatively simple (which is a good thing). Basically, as shown in Figure 1, the appliance sits between your administrative users and your VMware Infrastructure systems. It can be configured either as an Ethernet bridge or as a proxy. I personally prefer the bridge approach, since it doesn’t require client-side configuration and is much harder to circumvent – intentionally or on purpose.
Let’s look at the four basic functions individually:
Single Authentication Source
The appliance works in much the same way as vCenter Server – inbound administrative connections are terminated at the HyTrust appliance and HyTrust will use a single privileged account to perform host actions on the user’s behalf. The great thing about this approach is that you now have a single repository for user credentials – your Active Directory or other LDAP v3 repository. You don’t have to worry about keeping multiple authentication sources synchronized, and your users don’t have to remember a bunch of different passwords.
Granular Authorization Service
Because the HyTrust Appliance terminates inbound administrative connections, it has the ability to be very granular in its authorization functions. In addition to being able to authorize users for individual commands, such as esxcfgnas, you have the ability to authorize individual options on each command. For example, you could configure a role that has the rights to execute the command esxcfgnas -l but not esxcfgnas –a. This could be ideal for creating, for example, a role for an auditor who could come in and look at anything they wanted to, but they wouldn’t be able to change anything.
One of the really neat things that was demoed was a user connected to vCenter Server via the VIC attempting to execute a command that they are not authorized for. They were able to issue the command, but it was squashed even before it showed up as a task in the VIC status pane (and the attempt was logged). Ideally, unauthorized commands wouldn’t even show up in the UI, but the ability to prevent the command from even being scheduled for execution is a great first step.
Additionally, there is a single point for logging all actions performed against your environment.
Template-based Host Security Configuration
Another feature that was demonstrated was template-based host security configuration. OK, that sounds ominous – what exactly does it mean? It means that you can define the security settings that you want implemented for your hosts and the HyTrust Appliance can audit your hosts for compliance with your template and it can also remediate any hosts that it finds out of compliance. When the product ships, it will include two pre-defined templates that you can use out of the box or customize for your specific needs. The included templates will be base on the VMware ESX Security Hardening White Paper and the CIS VMware ESX Server Benchmark.
Additional templates may be added, and of course, you are free to create your own by modifying the included ones or starting from scratch.
Centralized Logging Facility
Since all administrative actions will be performed by the HyTrust Appliance, auditable logs can be created in one place. True, if you really have to dig in for forensics purposes, you’ll still have to go back to the source host and do log correlation and piece together an activity trail, but in many cases, you’ll have enough information in the HyTrust logs to satisfy your requirements. This can be a HUGE benefit for organizations that have regulatory obligations (such as HIPAA, GLBA, SARBOX, etc.) or for anyone who cares about security in general.
One of the things that I really liked about the log entries is that they were actually understandable! Here are just a couple examples to give you an idea:
- WARN : AUN0010I The request for {NetworkAdminUser {HT_NetworkAdmin}} to perform PowerOnVM_Task on VM : win2k3 is declined
- INFO : VVM0010O Source: 172.16.1.100 User: NetworkAdminUser Operation: RemoveVirtualSwitch
- INFO : AUN0001I The request for {NetworkAdminUser {HT_NetworkAdmin}} to perform RemoveVirtualSwitch on NETWORK : networkSystem-8 is authorized
There is enough information in the log to recreate the activities that a user has performed, the messages are structured to allow easy parsing by log analyzers, and the messages are clear enough that a human can read them and understand what’s going on.
Summary
I’ve not covered all the features that were presented in the demo, but I’ve hit what I felt were the high points. I’m eagerly awaiting the chance to put my hands on one of these boxes to put it through its paces for real.
In summary, I found the HyTrust Appliance to be a very interesting product that addresses many of the issues that nearly every virtualized environment is facing today. It enables true Role Based Access Control (RBAC) and single-source authentication for all of your VI administrative interfaces.
The only hole that I noticed in the HyTrust armor is the ESX server’s physical console. There is no way for a network-based product to protect against someone who has physical access to a system. This is true for every system and reinforces the best practice of ensuring the integrity of your security policies regarding access to systems.
As always, security is a combination of people, process, and technology. The HyTrust Appliance should be looked at by anyone who is serious about security in their environment.
Thanks Eric & Ken – I look forward to a product release in the near future!
More opinions can be found here:
Hytrust, virtualization under control @ Yellow Bricks / Duncan Epping
HyTrust Launches Security Appliance @ Scott Lowe
HyTrust: An Elegant Solution To a Messy Problem @ Rational Survivability / Chris Hoff
Virtually Secure – HyTrust Launches Virtual Security Appliance @ Professional VMware / Cody Bunch
9 responses to “HyTrust Appliance”
Trackbacks / Pingbacks
- - April 7, 2009
- - April 8, 2009
- - December 5, 2011
Ken,
I have been talking to Eric & Ken about their product since last year. They are sponsoring our May Wisconsin Area VMUG meeting.
The HyTrust Appliance is a very interesting product and has potential to solve several security and compliance concerns. I have not yet had the time to try it out live but I have gone through a couple of demos.
One of my main concerns I have expressed to the guys at HyTrust is that as I have seen it configured where the appliance is a single point of failure. If it fails and defaults to open access then you have a fairly simple way to bypass the security. It it fails and defaults to being locked down then you may have some real management problems until you can get it back online. You can still access the host from physical console but for some environments this is not real easy to do.
I would really like to see the ability to have the appliances configured with some failover capabilities. Outside of this I like what I have seen so far and am looking forward to seeing and learning more about what HyTrust has to offer.
What’s your thoughts on this?
Rod
Rod,
The single point of failure is an issue that I brought up with HyTrust. Their current answer is that you can stand up multiple appliances and do a manual failover between them. Their (near) future plans include something similar to clustered appliances with automated failover among the nodes.
Personally, I would be hesitant to deploy into a mission critical production environment without some sort of clustered / automated failover configuration, but I would definitely begin proof of concept testing and evaluation of feature set/capabilities since that is something that is going to take some time, anyway.
The HyTrust appliance is quite interesting and provides some much-needed functionality, but to really take advantage of it, an organization is going to have to do some planning and, likely, modify some of their processes/procedures (particularly around log analysis and auditing), so this is not something that’s going to go into production use for a while, anyway (at least that’s my take on it!)
Thanks,
KLC
Ken – any thoughts on how this product compare to Centrify DirectControl who does AD-based authentication/authorization/auditing for ESX and other virtualization platforms? e.g. http://www.centrify.com/resources/securing-vmware-esx-with-active-directory.asp with product specs etc. and http://www.centrify.com/directcontrol/vmware_esx.asp. More of a software-based approach vs. this appliance approach.
Thanks….
I’ve not had a chance to look at Centrify, so I can’t provide any feedback. I’ll put it on my agenda and get to it as soon as I can. Thanks for stopping by!
KLC
After my server crash, I moved from Vmware Server to Hyper-V. I wanted to go ESX, but I haven’t got hardware fully support by ESX. Nonetheless, using Hyper-V I’m extremely impressed by it’s speed and reliability.
Interesting, but what does it have to do with my article?